Workrise is an energy staffing company that uses its platform to connect skilled contractors in the energy industry with service providers and operators. In 2022, the company realized that in order to monitor, analyze, counter, and prevent security threats, it needed both a modern data lake as well as a security information and event management (SIEM) solution.
SIEM is not a new technology but one that has been evolving for years. Today, about 90% of SIEM solutions deliver capabilities exclusively in the cloud—up from 20% just three years ago. That’s because large volumes of data are at the core of SIEM, and only a cloud architecture offers the scalability needed to store and analyze petabytes of data.
Security is a data problem
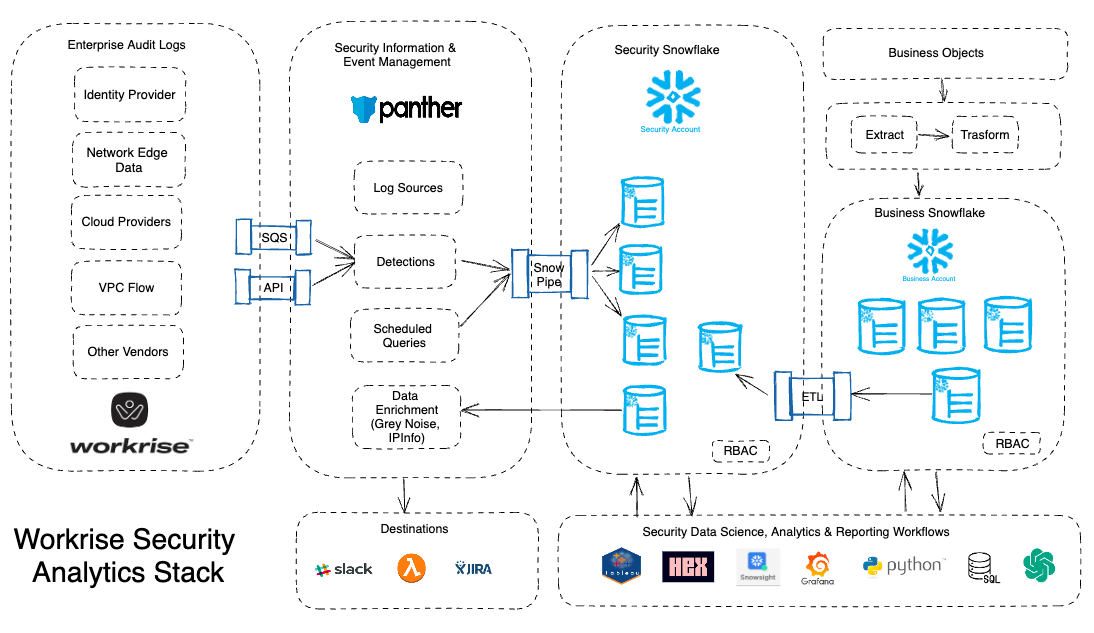
One of the challenges the company had in trying to address security threats was that Workrise had approximately 15 different enterprise systems and applications that generated log data. These included email logs, Google Drive logs, and endpoint logs from Cloudflare. Leveraging Snowflake, Workrise was able to improve the observability of its enterprise log sources and correlate across them by leveraging SQL, Python, and data science notebooks.
After an evaluation period, Workrise implemented Snowflake as its security data lake and Panther as its security analytics platform. The Workrise team ingested and centralized their critical logs into Snowflake so they could see patterns across multiple systems. Then, they conducted insight mining by querying the data on different topics. This allowed them to understand the data patterns, see areas that needed detections, and add them incrementally.
The modern security data lake
Using Snowflake as a security data lake provides several benefits. Snowflake allows you to unify your logs and enterprise data in a single place, eliminating data silos and making it easier to run advanced analytics. You can store virtually unlimited amounts of data cost-effectively for years, enabling you to identify patterns and trends that may not be visible with smaller data sets. This helps improve the accuracy of threat detection and response, and helps security teams identify and respond to new and emerging threats more quickly.
With Snowflake, you can combine contextual data sets with traditional security logs for higher-fidelity alerts and automate manual processes. Snowflake’s core architecture offers elastic compute power and instant scalability, allowing investigations to run quickly without worrying about concurrency, resource contention, compute power, scalability, or cost. You only pay for what you use—during a security event, you can quickly scale up to run searches, and then scale down again to save costs. Snowflake is also cloud agnostic, an important feature as more organizations pursue a multi-cloud strategy. And importantly, Snowflake is delivered as a service, saving DBA resources.
A strong security posture
Workrise has centralized all of its critical data, enabling visibility across different clouds and environments fourteen months after implementing a SIEM solution with Snowflake and Panther. New data logs are easy to ingest and analyze. Thanks to Snowflake’s scalable cloud architecture, Workrise can instantly run queries across years’ worth of data. The security team can also detect threats in real time and run faster investigations.
Workrise leverages Snowflake and Panther to detect, analyze, and mitigate a number of security threats, including:
- Insider threats: Security events inside the IT environment, such as compromised credentials, account manipulation, and data exfiltration.
- Account takeover: A third party gains access to an account and uses it for fraud, cyberattacks, and other malicious activities.
- Cloud resource misconfigurations: Errors, glitches, or gaps in the cloud environment, such as overly permissive access or default credentials for systems, that could pose a risk to valuable data.
- Brute force attack patterns: A trial-and-error hacking method where attackers submit several queries to gain unauthorized access to a system.
Workrise’s security team can use both its SIEM solution and Snowflake for threat hunting and responding to security incidents, and to form policies for identity access and management (IAM) and monitor third-party software usage in areas such as asset inventory. Additionally, Workrise enriches logs with ip-geolocation data (such as IpInfo) as well as known malicious IPs (GreyNoise) to improve the fidelity of detections with an overall improvement in the signal-to-noise ratio.
Next steps
With Snowflake and Panther, Workrise has gone from simply searching for threats to analyzing data in order to better understand threats, and then changing processes to decrease risks. In the future, Workrise plans to use AI and a security orchestration, automation, and response (SOAR) solution to automate security event response, freeing up data engineers for more value-creating endeavors.
To learn more about how Workrise leverages Snowflake and Panther to build a stronger security posture, check out the webinar here.
