With this blog post, I am publicly and officially launching something that people have been requesting from the Security Field CTO team for a very long time: Snowflake Security Dashboards. To get started, click the link to go to the quickstart. It’s live now and includes written instructions on how to create the tiles and add the SQL needed to make them work. To learn more about the project, however, and learn how it came to be, read on.
As a founding member of the Snowflake Security Field CTO team, I can tell you that customers invariably ask: Can we use Snowflake’s data superpowers to get to the bottom of our security and governance questions? The answer to this question has always been yes, and as Snowflake has evolved, the scope and depth of what the platform has been able to provide to strengthen security and governance has also evolved. Since day one, Snowflake has provided a comprehensive, built-in, secure audit log that records everything that your users do in Snowflake. But more recent advances have added more and more detail to that auditing. You can now achieve not just the security, but the detailed, multi-layered governance goals that you may have for this audit data.
One of our team’s most loved assets is the Snowflake Security Features Checklist. The Checklist (which should probably be called the Security & Governance Checklist, but that’s a different story) is an actionable version of the dense, rich information provided in the slides of the Snowflake Security and Trust Center. It has long provided a set of sample queries that you can use to better organize, analyze, and visualize your audit log information. But only recently with the launch of Snowsight and its out-of-the-box dashboarding can we now deliver a full UI to go with those queries.
We have no idea what our project will be named once it becomes a more official feature. Its purpose is clear, though: It provides an example of what a security dashboard can be in Snowflake.
But show is always better than tell, so let’s look at some dashboard charts.
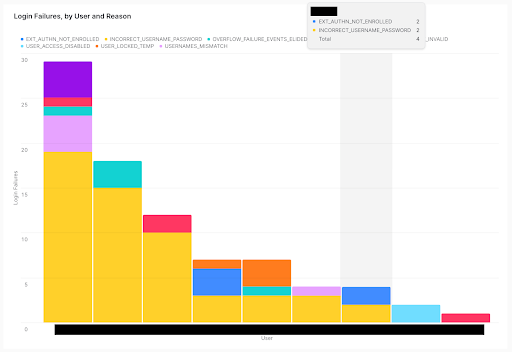
The chart in figure 1 cuts to the chase and looks at one of the best things a security pro will want to know: What login failure events are happening, by whom, and why. Knowing these details can help combat common attacks, like password spraying, credential stuffing, and more. Powered by the LOGIN_HISTORY View, this chart has every aspect of what customers most often ask us for, and hovering the mouse over a specific bar provides extra details about the data.

In figure 2, the chart’s “Most Dangerous Person” title may be a little cheeky, but the idea behind it is that you should know which user principles are granted the most rights. We could have gone with more technical names, like “Valid Accounts” or “Privilege Escalation” from the MITRE ATT&CK® framework that inspired this, but we like to have a little fun now and then.
The current version has about a dozen “tiles” like these two, and we are adding and reshaping them all the time as we learn from and with customers. Don’t see some detail that you know is in the audit logs but is missing from the tiles? That’s what’s great about this approach—you can add to it very easily, or remove things that you think are noise.
This announcement leads to many questions, but perhaps the most obvious is: What relationship does Snowflake Security Dashboards have to Snowflake’s Cybersecurity solutions?
In a very real sense, this is a microcosm of that very big effort. The biggest difference is focus. These dashboards focus exclusively on Snowflake itself. It’s using Snowflake to solve Snowflake-related security and governance problems, while the larger Cybersecurity workload solves arbitrarily large security and governance challenges for any and all systems—Snowflake included. But there really are no walls between the two. One of the big benefits of using Snowflake to build your Security Data Lake and solve cybersecurity challenges is that you can easily mix in data from the business that adds richness to the security point of view. The same is true for this project. If you have business data (e.g. user information from various applications) that would be cool to see right in the same charts as the built-in Snowflake audit trail, they are only a few clicks (or lines of SQL, Python, Java, and so on) away. In fact, these dashboards can be a first step into a wider world of using Snowflake as a security platform. Snowflake is just waiting for you to load in all those other audit trail logs to provide the charts more data. Of course, if you’re excited by the larger idea of Snowflake as a cybersecurity platform, we have a long list of partners who are delivering this for the whole scope of your security and governance data built on top of the power of Snowflake.
Another obvious question is: What about taking this analysis capability and using it to map to regulatory requirements, standards, and other extremely common frameworks that security and governance teams leverage?
Our team has you covered here, too. We’ve already started that work and we have mappings for NIST (800-53 & 800-171), HITRUST (CSF v9), MITRE ATT&CK (SaaS), and more. These assets require a signed NDA, but if your organization has already signed an NDA with Snowflake, you can get your hands on these assets by asking your friendly, neighborhood Snowflake Sales Engineer. Our mappings focus on this project and how these frameworks map to the Snowflake world.
These security dashboards take advantage of the fact that security and governance is primarily a data problem. Hopefully this gives you a taste of how excellent a solution Snowflake’s powerful capabilities can be for your security and governance needs. Our little project may be a pebble in that ocean, but it has opened the eyes of dozens of Snowflake customers, and with this push into public view, we’re eager to see how many more it can touch.
Our team is excited to get this into the world and we hope that you are excited to use this cool solution to start getting real answers to hard security and governance questions.
