As the cybersecurity threat landscape continues to evolve globally, organizations operating in the financial sector are seeing regulations shift to address the associated risks, and none may prove more impactful than the European Union’s (EU) Digital Operational Resilience Act (DORA). This regulation aims to strengthen the operational resilience of financial entities (FEs), and their third-party information and communication technology (ICT) providers.
Here, we’ll cover what DORA is, why it matters and how Snowflake can help support your DORA compliance obligations.
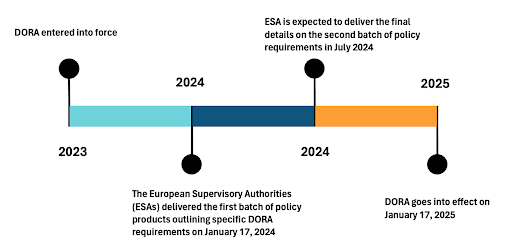
The second batch of DORA policy products, which aims to strengthen oversight and risk management for third-party ICT providers, is currently under development. Snowflake will provide more information once the second batch of policy requirements is established in July 2024.
DORA: Building a More Secure Financial System
DORA, enacted in January 2023, moves beyond reactive measures, requiring FEs and their service providers to proactively identify vulnerabilities, prevent disruptions and plan for swift recovery from incidents. DORA mandates a five-step lifecycle approach:
Identify: pinpoint critical functions vulnerable to disruptions.
Assess: evaluate the potential risks associated with those functions.
Prevent: implement robust measures to safeguard these functions.
Respond: develop clear plans for effectively handling incidents and minimizing their impact.
Recover: establish processes for rapid recovery after incidents to ensure business continuity.
This translates to several key requirements and their associated benefits:
- More stringent technical and process-oriented security measures, enhancing protection for both FEs and their ICT third-party providers.
- Identification of potential threats through data analysis and risk assessment processes to shift toward more proactive risk management.
- Collaboration between European Supervisory Authorities (ESA) and national competent authorities to promote consistent enforcement of cybersecurity rules and a more resilient financial ecosystem.
Five Core Pillars of DORA
1. ICT Risk Management Framework and Governance
FEs’ leadership teams must define a risk management strategy, inclusive of both their internally managed critical systems and the risks associated with their ICT providers. This strategy must incorporate business impact analyses as well as backup and recovery plans in the event of a security incident or loss of access to data.
2. ICT Incident Reporting
FEs must establish and implement a management process for monitoring, managing, logging, classifying and reporting ICT-related incidents. Depending on the severity of the incident, DORA specifies the incident notification timelines, forms and reporting requirements to both Competent Authorities (CA) and affected clients and partners.
3. Digital Operational Resilience Testing
FEs must test their ICT risk management framework periodically to evaluate the strength of the procedures and processes against any vulnerabilities. The results of these tests and any improvement plans against identified vulnerabilities must be reported to the CA, if requested.
4. Managing Third-Party Risk
FEs shall manage ICT third-party risk as an integral component of ICT risk within their ICT risk management framework. FEs must negotiate appropriate contractual arrangements when outsourcing functions to their ICT third-party service providers.
ESA will designate critical ICT providers in January 2025. All designated critical ICT third-party service providers will be subject to direct oversight by ESA.
5. Information Sharing Arrangements
FEs are encouraged to exchange cyberthreat and intelligence information among themselves, and to collectively leverage their individual knowledge and practical experience at strategic, tactical and operational levels. This will assist in enhancing their capabilities to adequately assess, monitor, defend against and respond to cyberthreats by participating in information-sharing arrangements.
How can Snowflake Help?
The Snowflake Data Cloud can be a valuable tool for FEs to achieve compliance with DORA and strengthen their overall operational resilience through robust security and advanced data management capabilities. When leveraged appropriately, Snowflake can and will empower FEs’ abilities to safeguard their sensitive financial data in compliance with their legal obligations.
Data Encryption: Snowflake encrypts data at rest using AES 256-bit (or better) encryption and leverages Transport Layer Security (TLS) 1.2 (or better) for data in transit. Snowflake’s Bring Your Own Key (BYOK) model (known as Tri-Secret Secure) empowers customers to maintain complete control over their encryption keys, adding an extra layer of security.
Access Control: Snowflake allows customers to define granular permissions for user roles, minimizing the risk of unauthorized access to sensitive data. Additionally, data can be classified and tagged based on its level of sensitivity, confidentiality or importance to the organization. This prioritizes security measures and simplifies data discovery.
Data Governance: Snowflake also offers a comprehensive list of data governance features. These include, but are not limited to, data masking, support for external tokenization and historical logging of user access history. These features further enhance the protection of customers’ sensitive data.
Data Resiliency: Snowflake understands the importance of data resiliency. Built-in fault tolerance and data replication supports continuous access to your data, even during hardware failures. Data is automatically replicated across different availability zones within the same region. If there’s an issue, the system automatically fails over to another zone, minimizing downtime.
Snowflake also offers advanced account replication and failover features (available in Business Critical and Enterprise editions). These features allow customers to replicate their entire Snowflake account, including databases and metadata, to a separate account in a different region, providing a complete disaster recovery solution. Replication is configurable, allowing customers to recover their data to a specific point in time, if necessary. By combining industry-leading security features with robust disaster recovery options, Snowflake provides a comprehensive solution for safeguarding your sensitive financial data.
Third-Party Monitoring: Snowflake has an established vendor risk assessment program, which evaluates the operational resilience of its sub-processors annually and on an ad hoc basis. Snowflake customers may subscribe at the above link to receive advance notifications of new sub-processors.
Proactive Security: Snowflake conducts frequent vulnerability scans and engages third-party security firms to conduct penetration testing of its platform. Snowflake also integrates with popular Security Incident and Event Management (SIEM) systems, allowing Snowflake customers to centralize security monitoring and receive alerts of suspicious activity. In the event of a security incident, Snowflake will provide its customers with timely information about the nature and consequences of the incident, the measures being taken to mitigate it, and the status of their investigation as described in Snowflake’s Security Addendum.
* * *
By leveraging Snowflake’s capabilities, FEs gain a strong partner in navigating DORA’s requirements, empowering them to build a more secure and trusted financial landscape.
To learn more about our commitments, please contact Snowflake or reach out directly to your Snowflake Account Team for early access to guidance material.
This blog post is provided for informational purposes only, with the understanding that it shall not create any legally binding representations or other obligations on Snowflake or constitute legal advice. Snowflake serves a variety of Customers with organization-specific deployment models and regulatory compliance demands, and you are responsible for making your own independent assessment of the information contained herein and ensuring your own compliance with all applicable laws and regulations. You should consult with your legal advisors for any requirements associated with the compliance posture of your organization. Snowflake may update the information provided in this document from time to time without notice.
